
DAOs were supposed to be the future of decentralized decision-making. No bosses. No middlemen. Just code and community. But over the last few years, they’ve become the most targeted targets in crypto - not because of weak code, but because of governance flaws. And the losses? They’re not small. We’re talking about $300 million+ stolen in just a few major attacks. If you’re part of a DAO or thinking about joining one, you need to understand how these hacks actually work - and how to protect yourself.
How DAO Hacks Actually Happen
It’s not what you think. Most people assume DAO hacks happen because of buggy smart contracts. Sure, that happens sometimes. But the biggest, most devastating attacks? They exploit the governance system. The very thing that was supposed to make DAOs fair and democratic became their weakest link. Take the Beanstalk attack in April 2022. The attacker didn’t break into a wallet. They didn’t guess a private key. They used a flash loan - a loan you take and repay all within one blockchain transaction. With that loan, they borrowed over $180 million worth of Beanstalk tokens. Suddenly, they controlled 79% of the voting power. They submitted a proposal to drain the treasury. It passed. They walked away with $76 million. And by the time anyone noticed, the transaction was already confirmed. There was no undo button. This wasn’t luck. It was design.The Three Biggest DAO Attack Vectors
After analyzing over a dozen major DAO breaches, security researchers have identified three consistent patterns:- Flash loan exploitation - Borrowing huge amounts of voting tokens temporarily to control governance votes, then repaying the loan before anyone can react.
- Off-chain voting manipulation - Attackers monitor private proposal discussions before they go public. They buy up tokens, stack votes, and push through malicious changes before the community even knows what’s coming.
- Token-based coercion - A few big holders (or coordinated groups) use their token weight to bully votes. Sometimes it’s PR campaigns. Sometimes it’s direct bribes. Sometimes it’s just sheer influence. Either way, the "one token, one vote" ideal breaks down fast.
And don’t forget proposal spamming. Some attackers flood the system with 50+ low-effort proposals just to clog up the queue. Legitimate upgrades? Forgotten. Community attention? Drained. Time? Wasted.
Why DAO Governance Is Broken
The core problem? Voting power is tied directly to token ownership. If you own 10% of the tokens, you get 10% of the vote. Sounds fair. Until someone can borrow $200 million in tokens for 10 seconds and swing a vote. DAOs assume everyone acts in good faith. But crypto attracts people who exploit loopholes - not because they’re evil, but because the system lets them. There’s no identity verification. No human review. No cooldown period. No way to say "wait, this doesn’t make sense." Even "sophisticated" DAOs like Uniswap and Arbitrum have fallen victim. Why? Because they never designed for bad actors. They designed for idealists.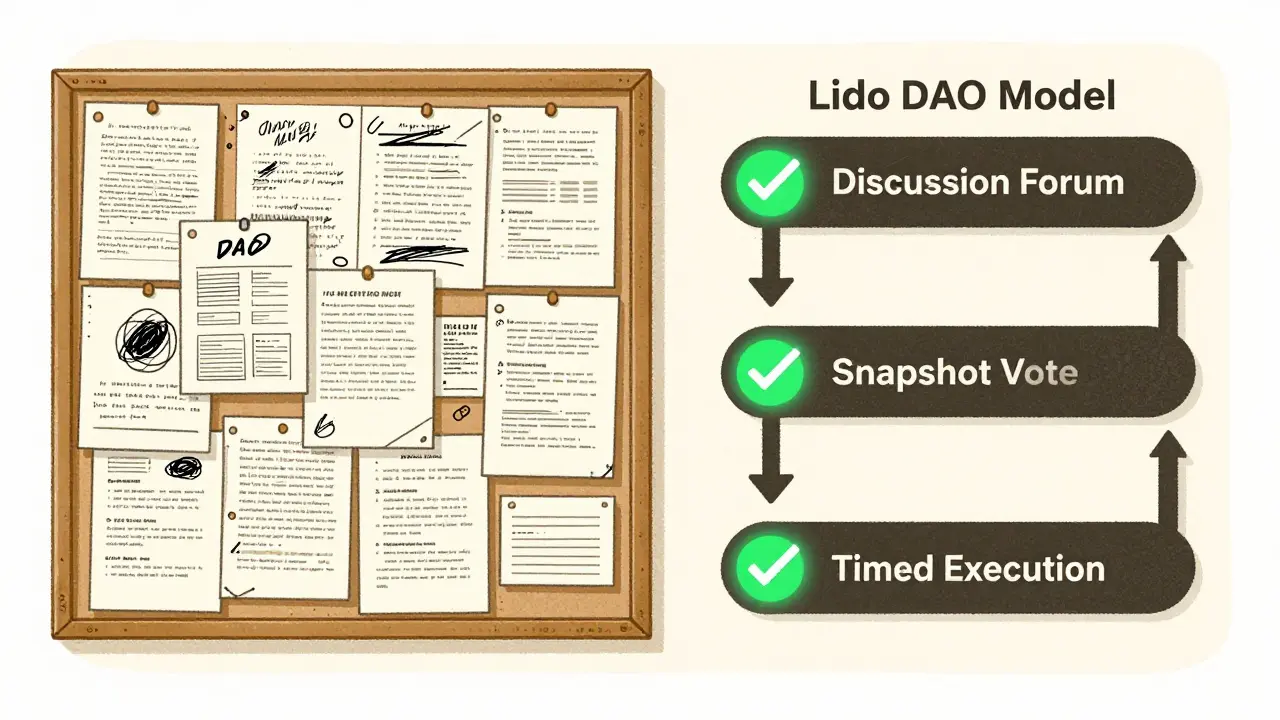
What Works: The Lido DAO Model
Not all DAOs are sitting ducks. Lido DAO is one of the few that actually got it right. Their process has three clear steps:- Discussion - Proposals are debated publicly on forums. Anyone can comment. No secret meetings.
- Off-chain voting - Before going on-chain, they run a gas-free vote using Snapshot. This gives the community time to react, spot red flags, and call out suspicious proposals.
- On-chain execution - Only after off-chain consensus do they lock in the vote on the blockchain.
This isn’t perfect - but it adds breathing room. Time is the best defense against flash loan attacks. If you have 48 hours to review a proposal, you can spot a manipulation. If it goes live in 10 minutes? You’re toast.
DAOIP-8: The Security Standard No One’s Following
A group called DAOstar built a framework called DAOIP-8 - a set of minimum security controls for DAOs. It’s not theoretical. It’s practical. And almost no DAO follows it. Here’s what DAOIP-8 says you need:- Timelocks - No governance change should execute immediately. At least 48-72 hours between vote approval and execution.
- Quorum thresholds - Don’t let a 5% vote change your treasury. Require 10-20% participation for major changes.
- Simulation before execution - Test proposals on a forked version of the chain first. See what happens before you commit.
- Automated checks - Block proposals that try to drain funds, change admin keys, or remove timelocks.
- Emergency response plans - Who do you call? What’s the backup? How do you pause the system if something goes wrong?
Simple. But rarely done. Most DAOs skip timelocks because "it slows things down." But speed isn’t freedom - it’s recklessness.

The Future: Zero-Knowledge Proofs and Decentralized Identity
The next wave of DAO security isn’t about more votes. It’s about better verification. Researchers are testing:- Zero-knowledge proofs - Letting users vote without revealing their token holdings. This stops coercion. You can’t bribe someone if no one knows how many tokens they own.
- Soulbound Tokens - Non-transferable tokens that prove you’re a real, long-term participant - not a bot or a bought account.
- Proof of Humanity - Verifying that voters are real people, not sybil accounts.
These aren’t sci-fi. They’re being tested in early-stage DAOs. But adoption is slow. Why? Because they’re harder to build. They require more code. More testing. More trust in new systems.
What You Should Do Right Now
If you’re a DAO member:- Never vote on a proposal without reading the full details. Look for sudden fund transfers, admin key changes, or removal of timelocks.
- Check if the DAO uses Snapshot for off-chain voting. If not, walk away.
- Join the community forum. Most attacks are spotted there - before they go on-chain.
- Ask: "What’s the timelock?" If they don’t know, they’re not secure.
If you’re launching a DAO:
- Start with DAOIP-8. Don’t invent your own system.
- Require a 72-hour timelock for all treasury changes.
- Use Snapshot for off-chain voting. Make it mandatory.
- Simulate every proposal. Use a testnet fork.
- Don’t rush. Security isn’t a feature - it’s the foundation.
Why This Matters Beyond Money
Every DAO hack doesn’t just steal money. It steals trust. When a DAO gets drained, people stop believing in decentralization. They start thinking: "This is just another Wall Street scam with blockchain buzzwords." And that’s worse than the loss itself. The beauty of DAOs was that they promised fairness. But fairness only works if the system is designed to resist abuse. Right now, most DAOs are like a bank with no locks on the vault - and they’re surprised when someone walks in. The fix isn’t harder code. It’s better habits. Slower decisions. More transparency. And never, ever trusting the speed of automation over the wisdom of the crowd.Can a DAO be hacked even if the smart contract is secure?
Yes. In fact, most major DAO hacks didn’t exploit code bugs - they manipulated governance. A perfectly secure smart contract can still be drained if an attacker gains enough voting power through flash loans, bribes, or off-chain coordination. Security isn’t just about code - it’s about how decisions are made.
What’s a flash loan attack and how does it work?
A flash loan attack lets an attacker borrow a huge amount of tokens - millions or even billions - for a few seconds, with no collateral. They use that borrowed power to vote on a malicious proposal (like transferring all funds out), execute it, then repay the loan in the same transaction. Because the loan is repaid, the blockchain accepts it as valid. No one can stop it in real time.
Why don’t DAOs just use a 24-hour timelock?
Many do - but not enough. Some DAOs skip timelocks because they want "fast decisions." But speed creates vulnerability. A 24-hour timelock gives the community time to spot bad proposals. A 10-minute timelock? That’s just a speed bump for attackers. Experts recommend 48-72 hours for anything that touches the treasury.
Are DAOs with large token holders more vulnerable?
Yes. When 1-5 wallets hold over 30% of voting power, the DAO becomes a plutocracy - not a democracy. These holders can push through proposals without community support. Attackers often target these DAOs because they know they can buy influence or coordinate with insiders. True decentralization requires broad distribution of tokens - not concentration.
What should I look for before joining a DAO?
Ask four questions: 1) Do they use Snapshot for off-chain voting? 2) Is there a timelock on treasury changes? 3) Are proposals publicly discussed before voting? 4) Is there a documented incident response plan? If the answer to any of these is "no," the DAO is at high risk. Don’t invest your tokens until you’re confident.



Angela Henderson
February 16, 2026 AT 04:53Man, I’ve been in a couple DAOs and honestly? I just scroll past the proposals unless it’s something about token swaps or new partnerships. The rest feels like reading legal docs in a language I don’t speak. I don’t even know what a timelock is supposed to do, and I’m supposed to vote on it? I’m not a coder. I just want to know if my tokens are gonna be safe. And honestly? Most DAOs don’t even explain it in plain English. It’s like they’re proud of being confusing.
Paul David Rillorta
February 16, 2026 AT 10:38lol so the ‘decentralized’ system is just a glorified stock market where billionaires borrow money to vote themselves richer? classic. they’re not hacked, they’re *designed* to be robbed. flash loans? more like flash *heists*. and don’t even get me started on ‘snapshot’-that’s just a voting app that lets the same 5 whales vote 3 times a week. the whole thing is a scam. crypto isn’t broken. it was NEVER meant to be fair. they just made it look pretty so dumb people would throw money at it. #wakeuptwitter
Lauren Brookes
February 17, 2026 AT 04:24I think the real issue isn’t just the technical flaws-it’s the assumption that people will act rationally. We’re not robots. We’re humans with emotions, biases, and incentives. A flash loan attack works because it exploits not just the system, but the hope that others will care enough to stop it. What if we stopped designing DAOs around ‘perfect efficiency’ and started designing them around ‘human patience’? What if we built in silence? A mandatory 72-hour cooling-off period where you can’t vote unless you’ve read 3 different summaries, watched a 5-minute explainer, and posted one comment in the forum? It sounds slow. But maybe slow is the only way to be safe.
Andrew Edmark
February 17, 2026 AT 21:44Hey everyone, I just wanted to say I really appreciate how thoughtful this post is. It’s easy to get frustrated with DAOs, but this breaks it down in a way that actually helps. I’ve been in a few DAOs where I felt like I was just a number-my vote didn’t matter because some whale had 30% of the supply. But reading about Lido’s process? That gives me hope. We don’t need to be perfect. We just need to be intentional. If you’re new to DAOs, don’t be afraid to ask questions. Seriously. The community’s better than you think. And if no one’s answering? That’s a red flag too. 💙
Dominica Anderson
February 18, 2026 AT 04:16It’s not a governance flaw-it’s a failure of the American dream. You can’t have democracy without merit. DAOs are for people who think ‘voting’ is a magic spell. If you don’t understand flash loans, you shouldn’t be voting. Period. This isn’t a bug. It’s evolution. The strong survive. The rest? They get liquidated. Welcome to crypto.
Aileen Rothstein
February 20, 2026 AT 03:59Okay but have you seen what’s happening in the Arbitrum DAO right now? They just passed a proposal to shift 12% of the treasury to a new ‘infrastructure fund’-and the proposal had 3 typos. THREE. And it passed with 80% approval. I checked the voter distribution-47% came from two wallets that didn’t even show up in the forum. That’s not governance. That’s a glitch in the matrix. And the worst part? No one’s mad. They’re just like, ‘oh cool, new funding.’ Bro. We’re being played. We need to stop treating this like a game and start treating it like our money.
Jennifer Riddalls
February 20, 2026 AT 20:09just wanna say i read the whole thing and i feel way more informed now. i used to think dao security was just about smart contracts but now i get it-its all about the people. and the time. and the space to breathe before you vote. if a dao doesnt have snapshot or a timelock? im out. no hard feelings. just not worth it. thanks for writing this. really. 🙏
Jeremy Fisher
February 22, 2026 AT 01:35Back in my day, we didn’t have flash loans or snapshot or timelocks. We had trust. And if you broke that trust? You got kicked out. Not by code. By community. I’ve lived in Japan, Kenya, and now here in the States, and one thing’s consistent: systems that move too fast break. DAOs are trying to build democracy on rocket fuel. We need to slow down. Not because we’re lazy, but because we’re human. A 72-hour window isn’t slow-it’s sacred. It’s the time you need to talk to your neighbor, read the proposal three times, and ask yourself: ‘Does this make sense?’ If the answer’s no, don’t vote. Just wait. Let the noise settle. That’s not inefficiency. That’s wisdom.
Anandaraj Br
February 23, 2026 AT 13:52bro why u even care? dao is just a new way to get rich quick. u think lido is safe? they got 300m in steth. who’s really in charge? the same people who started it. its all fake decentralization. u think snapshot stops attacks? nah. they just move the attack to discord. u think timelock helps? nah. the whale just buys more tokens overnight. this whole thing is a cult. stop pretending its about fairness. its about who owns the keys. and guess what? u dont. u just think u do.
AJITH AERO
February 23, 2026 AT 18:00so the solution is… more bureaucracy? lol. next you’ll say we need a DAO of DAOs to audit the DAOs. can we just shut it down and go back to banks? at least they have customer service.